8 Tips to spot phishing scams
What is Phishing?

The Go-To Social Engineering Strategy
Phishing is the art of tricking you into giving away
sensitive information or downloading malicious software
onto your PC or company network. Nowadays, it is far
easier for a criminal to manipulate you to do something
than it is to manually hack into your computer or your
company’s network.
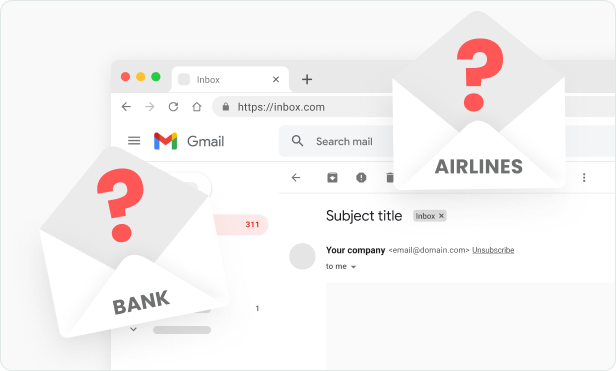
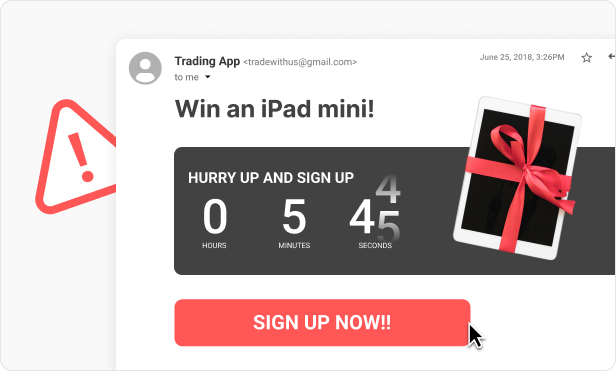
Phishing is easily carried out over email, it is
inexpensive and can be repeated over and over to large
lists of recipients. Phishing emails are often
interesting. They are created in a way that can
influence you to take action, and as a result can look
very realistic.
Phishing Attack Methods
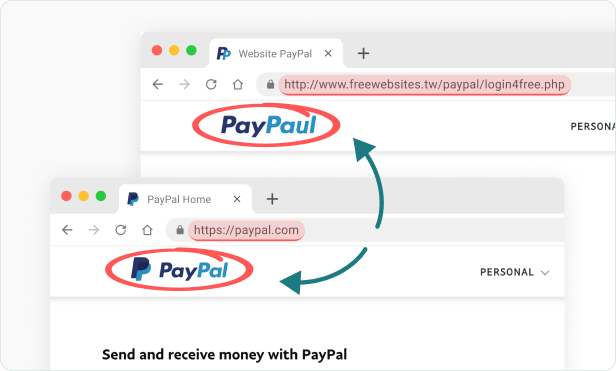
Deceptive Phishing
An attack where criminals impersonate a legitimate person or company that isn't very targeted.


Spear Phishing
A personalized attack where the criminal uses tailored information to make the email more appealing to you.

Whaling
A specialized type of spear phishing that targets an important figure within a company.

Everyone is a Target Always Be Aware of Phishing
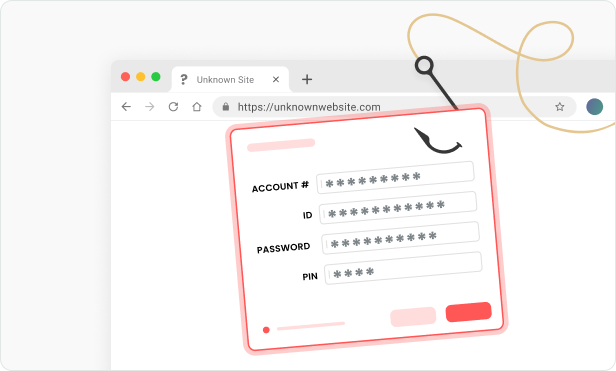
Email Phishing
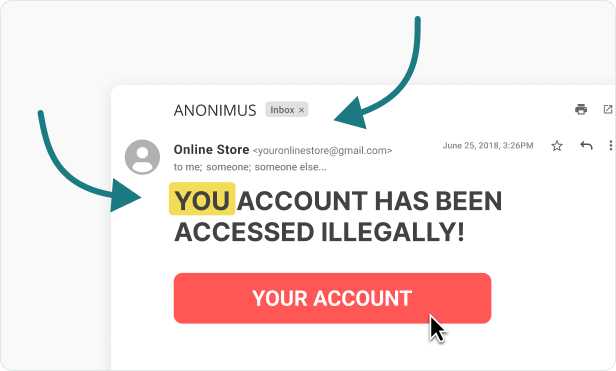
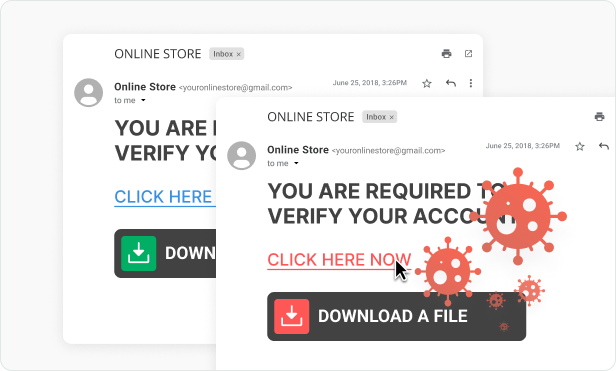
Criminals send phishing emails that appear to come from valid sources in an attempt to trick you into revealing personal, financial or company information.
What to look out for?
Spear phishing is harder to spot...
Hi all,
Next week we will experience internet downtime due to a network upgrade from BT. Although expected overnight, this period of no connectivity might carry over to the following morning.
For more information on dates and arrangements made around this issue please go to
Invalid Link
Regards,
http://www.ma1ware-bounc1ng.biz
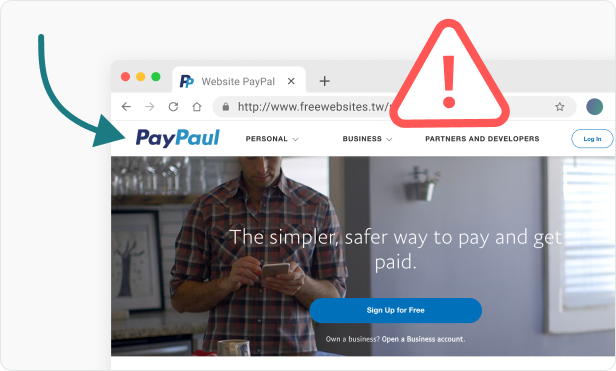
Misleading and Invalid Link
Exam
Please select the correct answer
question2
Exam Results
Your result is: 5 out of 10
5-Minute Phishing Quiz

Quiz Completed
You finished the phishing quiz.
 Correct:
1 /
9
Correct:
1 /
9
Is this a phishing mail?
Find out if the email could be a phishing attempt and click either "regular email" or "phishing email".
You can use hints during the game. The "next" button will take you to the next game question.

 Incorrect
Great Job!
Incorrect
Great Job!
This is a phishing mail.
This is a regular mail.